Hello 👋, Application Monitoring is critical for your business. It gives vital information on your customer experience. Monitoring your system and infrastructure is essential to ensure the performance of your services. As software development moves faster and faster, alerting and monitoring becomes an indispensable practice for modern DevOps teams.
The cloud applications' monitoring platform has to bring together data from servers, containers, databases, identity management, and third-party services to make the stack entirely observable.
In this post, we will see how we can stream Auth0 logs to Datadog to monitor, alert, and analyze Auth0 events.
Prerequisites
Setup Auth0 Log Streaming
The first step is to setup log streaming from the Auth0 dashboard.
Log in to the Auth0 Dashboard.
Navigate to Logs > Streams.
Click "Create Stream."
Select Datadog, and enter a unique name for your new Datadog Event Stream.
On the next screen, provide the following settings for your Datadog Event Stream: API Key & Region. Click Save.
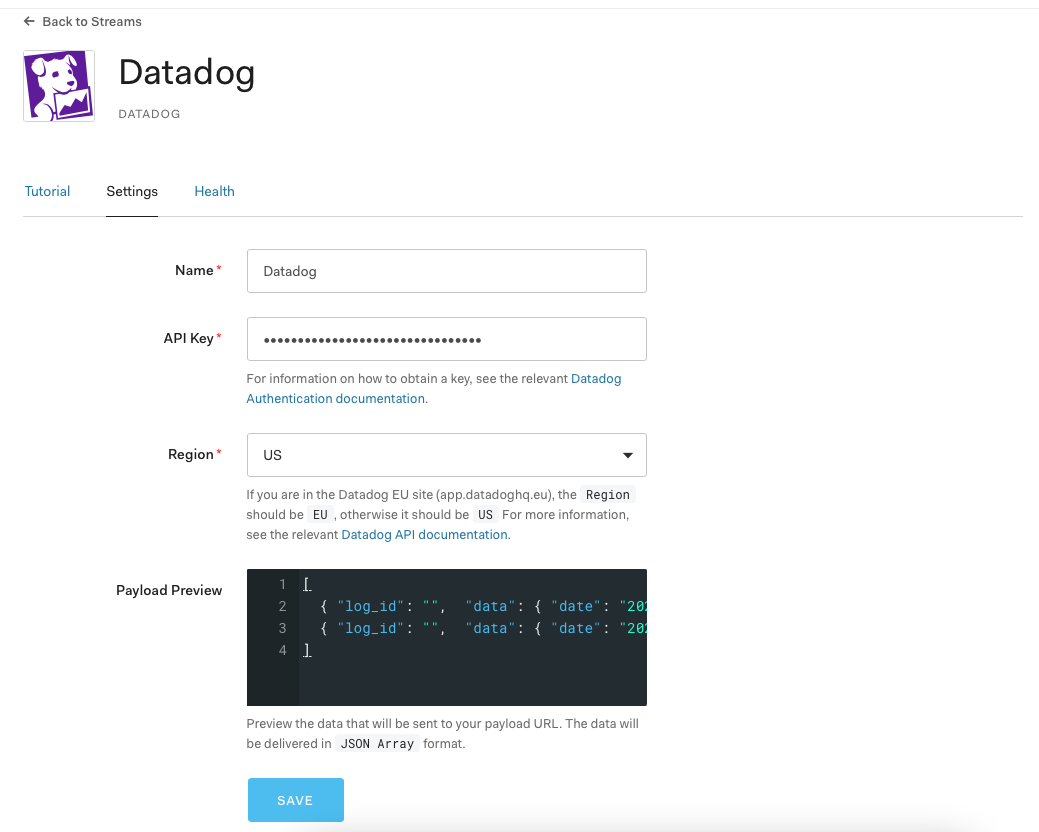
The setup is done. When Auth0 writes the next log event, the log events are streamed to Datadog.
Monitor Auth0 Activities
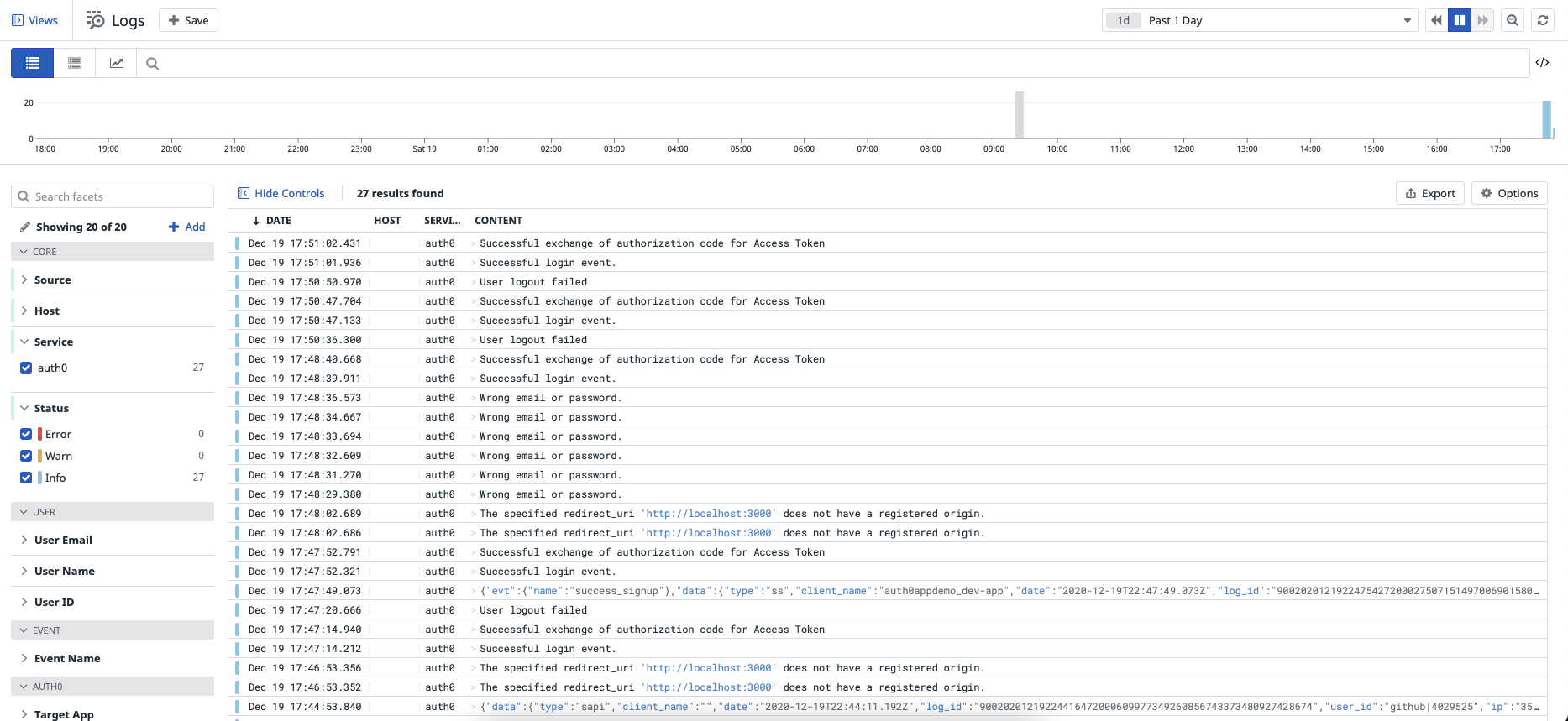
As Auth0 streaming the logs to Datadog to ingest, it sends them through a log processing pipeline. The pipeline automatically parses each log to extract key data as standard attributes, which provide a naming convention you can use to correlate events from multiple sources easily.
Auth0 has a set of event types with code and description. Datadog automatically maps the Auth0 event type code to the event name. You can use this Event Name facet to analyze user activity such as account creation and deletion, password changes, and more.
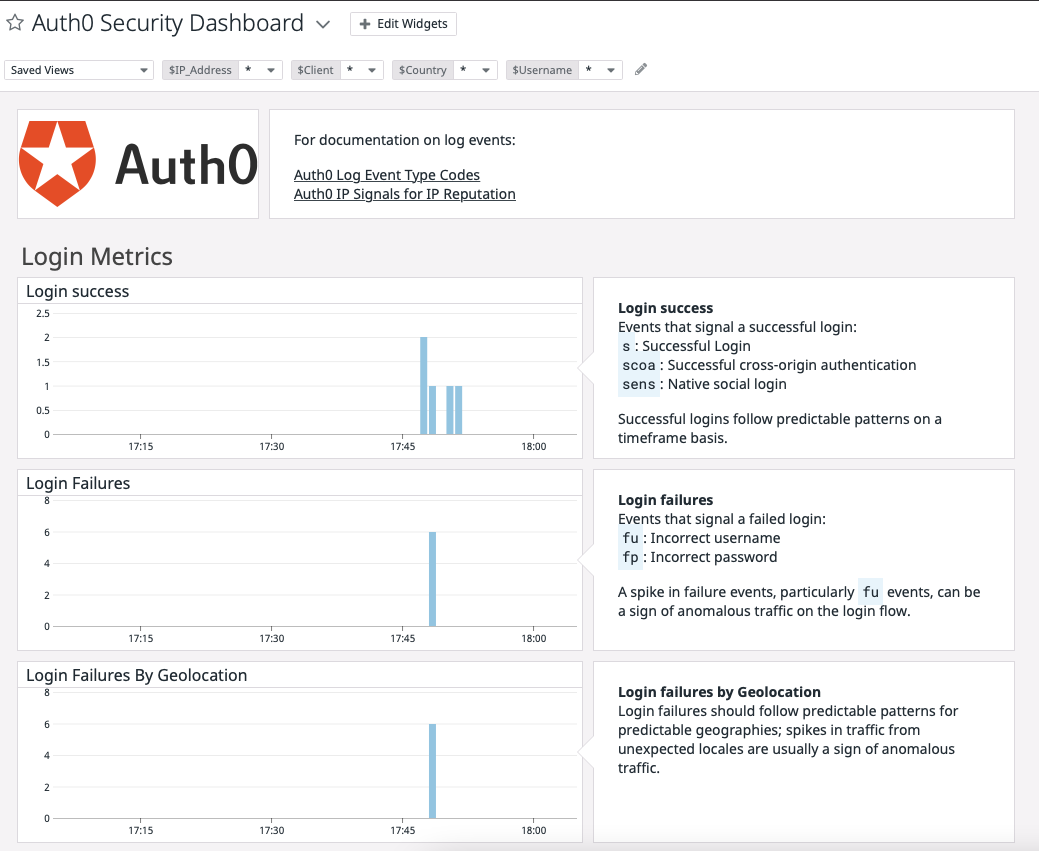
Security Dashboard Visualization
If you want to visualize the Auth0 events using Datadog dashboards, Auth0 is providing the dashboard template to import in Datadog to visualize the metrics captured from the log stream.
The dashboard provides the recommended aggregations to view, and you can customize the visualization based on your needs.
Download the dashboard template here. Import the JSON file in the Datadog Dashboard section created using the Screen Board Dashboard type.
Alerts and Threat Notification
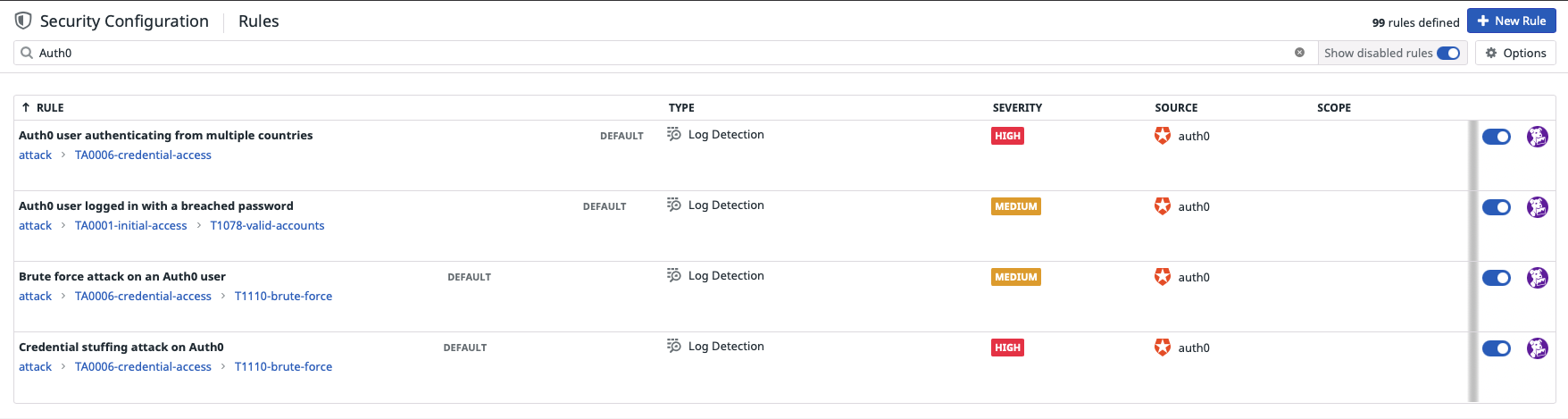
Datadog's new Detection Rules give you a powerful way to detect security threats and suspicious behavior within all ingested logs in real-time. You can create the detection rules by defining conditional logic to the Auth0 log stream. If the rule is matched, Datadog evaluates the security and notify.
Datadog has pre-defined detection rules for Auth0 source.
- Auth0 user authenticating from multiple countries - High
- Auth0 user logged in with a breached password - Medium
- Brute force attack on an Auth0 user - Medium
- Credential stuffing attack on Auth0 - High
You can also create custom rules with conditions. Datadog analyzes Auth0 logs to detect any violations and alert your team via notification channels or incident management system.
Conclusion
Auth0's log streaming service streams the events and logs to a host of integration partners, such as Amazon EventBridge, Azure EventHub, Datadog, Splunk, Sumologic, and custom webhooks.
Log / Event streaming helps to export the log, take decisions based on the events for threat detection and notifications, and also process identity-information in near real-time. It also helps to set up the additional data pipelines for processing based on the Auth0 events using Amazon Event Bridge or Amazon Event Hub in Event-driven applications.
Please follow me on my twitter, linkedin and github for more articles/demos on security, cloud native, containers and mobile/web apps.
